Kubernetes checks if the container is alive through Liveness
Probe and it will let kubelet to know when to restart a container. We can
specify a liveness probe for each container in the pod specification.
Kubernetes will periodically execute the liveness probe and restart the
container if the probe fails.
Kubernetes can probe the container in three different ways.
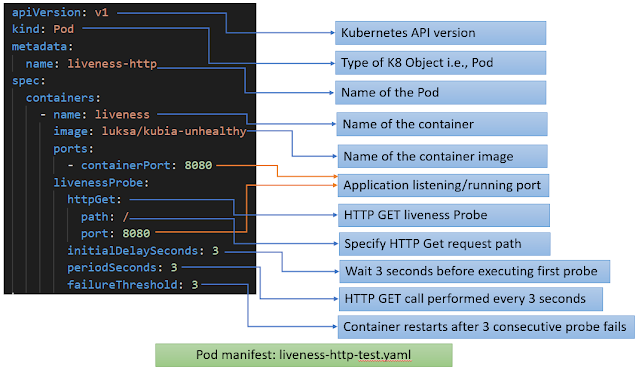
1. HTTP GET probe
It performs an HTTP GET request on the container’s REST API
resource. If the probe receives a response code between 2xx to 3xx is considered
successful. If Http server returns different response code (i.e. other than 2xx
to 3xx) or if it doesn’t respond at all, the probe is considered a failure and
the container will be restarted by kubelet.
As per code written in the specified node.js app, Http GET
request returns response code as 500 after each fifth request. So, Pod will
restart automatically after 3 consecutive failures.
3. Exec probe
It executes a specified command inside the container and checks the command’s exit status code. If the status code is 0, the probe is successful. Otherwise, the container will be restarted by kubelet.
Effective liveness probe check
you should always define a liveness probe. Without one, Kubernetes has no way of knowing whether your app is responding to HTTP requests. So, liveness probe helps us to restart the container when the application is unresponsive state.
- Configure the liveness probe to perform request on a specific URL path (i.e. /health)
- Make sure HTTP GET /health does not require validation or authentication
- Always check only internals of the app and should not depend on external services/dependencies.
- liveness probe should not return a failure when the server cannot connect to the database. If the underlying cause is in the database itself, restarting the web server container will not fix the problem.
- HTTP GET /health probe should not use many computational resources and should not take too long to complete. It supposed get response back in one second.
- liveness Prob failureThreshold default value is 3. So, it is not mandatory to specify again in pod yaml file.
- Do not set the same specification for Liveness and Readiness Probe
- Try to avoid "exec" probes as there are known problems with them
- Exit the process when uncaught exception occurs (i.e. kubelet will restart the container automatically) instead of signaling to liveness probe
- Liveness probe should be used as a recovery mechanism only when the process is not responsive.
- Kubernetes for Developers #25: PersistentVolume and PersistentVolumeClaim in-detail
- Kubernetes for Developers #24: Kubernetes Volume hostPath in-detail
- Kubernetes for Developers #23: Kubernetes Volume emptyDir in-detail
- Kubernetes for Developers #22: Access to Multiple Clusters or Namespaces using kubectl and kubeconfig
- Kubernetes for Developers #21: Kubernetes Namespace in-detail
- Kubernetes for Developers #20: Create Automated Tasks using Jobs and CronJobs
- Kubernetes for Developers #19: Manage app credentials using Kubernetes Secrets
- Kubernetes for Developers #18: Manage app settings using Kubernetes ConfigMap
- Kubernetes for Developers #17: Expose service using Kubernetes Ingress
- Kubernetes for Developers #16: Kubernetes Service Types - ClusterIP, NodePort, LoadBalancer and ExternalName
- Kubernetes for Developers #15: Kubernetes Service YAML manifest in-detail
- Kubernetes for Developers #14: Kubernetes Deployment YAML manifest in-detail
- Kubernetes for Developers #13: Effective way of using K8 Readiness Probe
- Kubernetes for Developers #12: Effective way of using K8 Liveness Probe
- Kubernetes for Developers #11: Pod Organization using Labels
- Kubernetes for Developers #10: Kubernetes Pod YAML manifest in-detail
- Kubernetes for Developers #9: Kubernetes Pod Lifecycle
- Kubernetes for Developers #8: Kubernetes Object Name, Labels, Selectors and Namespace
- Kubernetes for Developers #7: Imperative vs. Declarative Kubernetes Objects
- Kubernetes for Developers #6: Kubernetes Objects
- Kubernetes for Developers #5: Kubernetes Web UI Dashboard
- Kubernetes for Developers #4: Enable kubectl bash autocompletion
- Kubernetes for Developers #3: kubectl CLI
- Kubernetes for Developers #2: Kubernetes for Local Development
- Kubernetes for Developers #1: Kubernetes Architecture and Features
Nice explanation.
ReplyDeleteIt is so helpful for fresher in k8s.
Very good short notes and samples on each topic. Helpful for even experienced for reference.
ReplyDelete